Spectre Vulnerability – How to Patch VMware ESXi
As per the initial VMware Security Advisory, the specified patches should be applied for remediation. Remember, these patches remediate known issues. Watch for additional patches as exploits may continue to surface. If you are needing to patch your ESXi host per the advisory, you can do so through VMware Update Manager (VUM).
Update – VMware has updated patches to address Hypervisor-Assisted Guest Mitigation (VMSA-2018-0004).
As a recap, patches have been released to address Hypervisor-Specific Remediation (VMSA-2018-0002) and Hypervisor-Assisted Guest Remediation (VMSA-2018-0004). For more detail on mitigation types, check out this VMware KB. In addition to hypervisor patches, VMware has also released patches for vCenter and other virtual appliances (VMSA-2018-0007). Installation instructions can be found here.
VMware Patch Numbers for Hypervisor-Specific Mitigations (VMSA-2018-0002):
- ESXi 6.5 – ESXi650-201712101-SG
- ESXi 6.0 – ESXi600-201711101-SG
- ESXi 5.5 – ESXi550-201709101-SG
- This 5.5 patch only addresses CVE-2017-5715, not CVE-2017-5753
VMware Patch Numbers for Hypervisor-Assisted Mitigations (VMSA-2018-0004):
- ESXi 6.5 – ESXi650-201803401-BG, ESXi650-201803402-BG
- ESXi 6.0 – ESXi600-201803401-BG, ESXi600-201803402-BG
- ESXi 5.5 – ESXi550-201803401-BG, ESXi550-201803402-BG
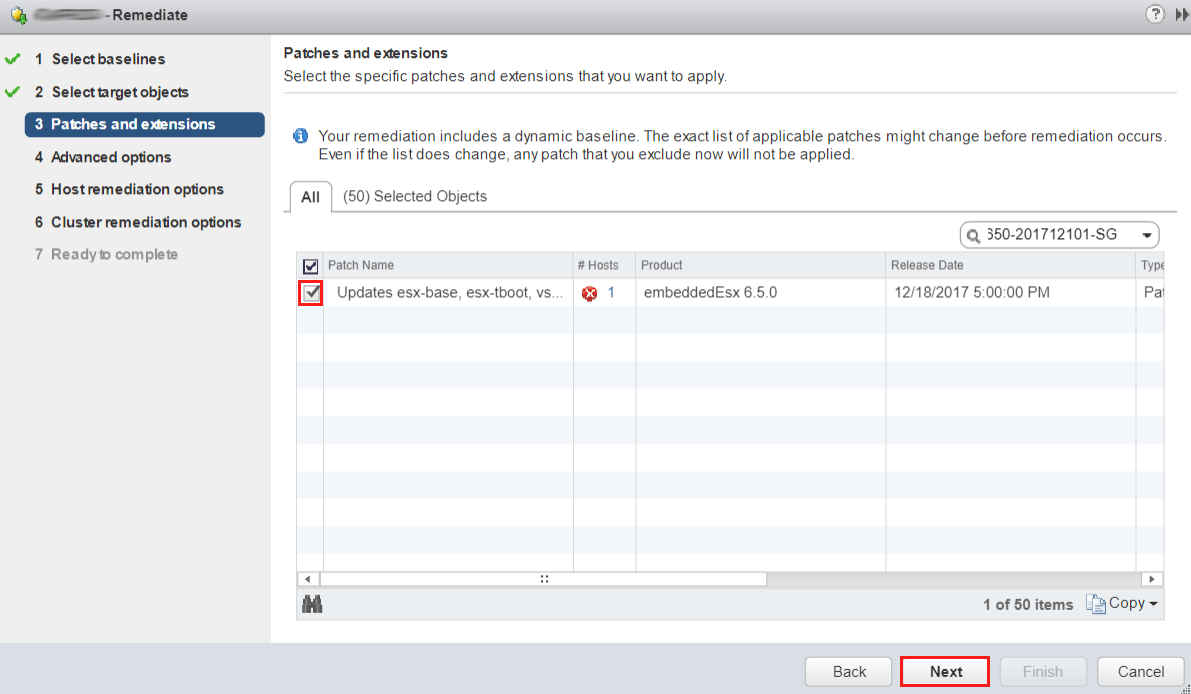
For this example, we will be patching VMware ESXi 6.5 with patch ESXi650-201712101-SG. Additional patches can be applied in the same manner. Read the release notes or security advisories before patching as other components (ie. vCenter) may need to be patched first.
Remediate ESXi
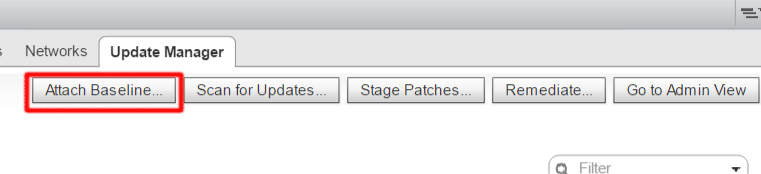
Let’s begin! Log in to the vSphere web client and select the host or cluster for remediation. Locate the Update Manager tab and select Attach Baseline.
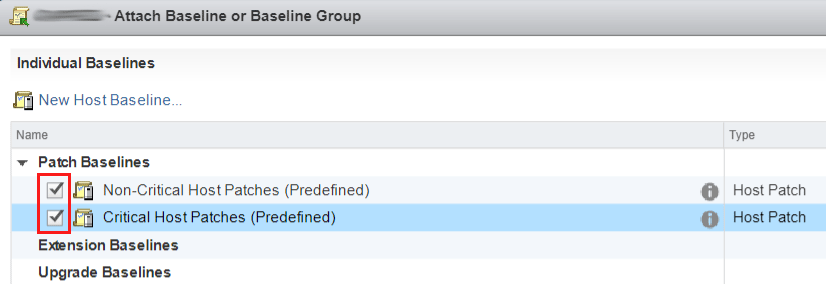
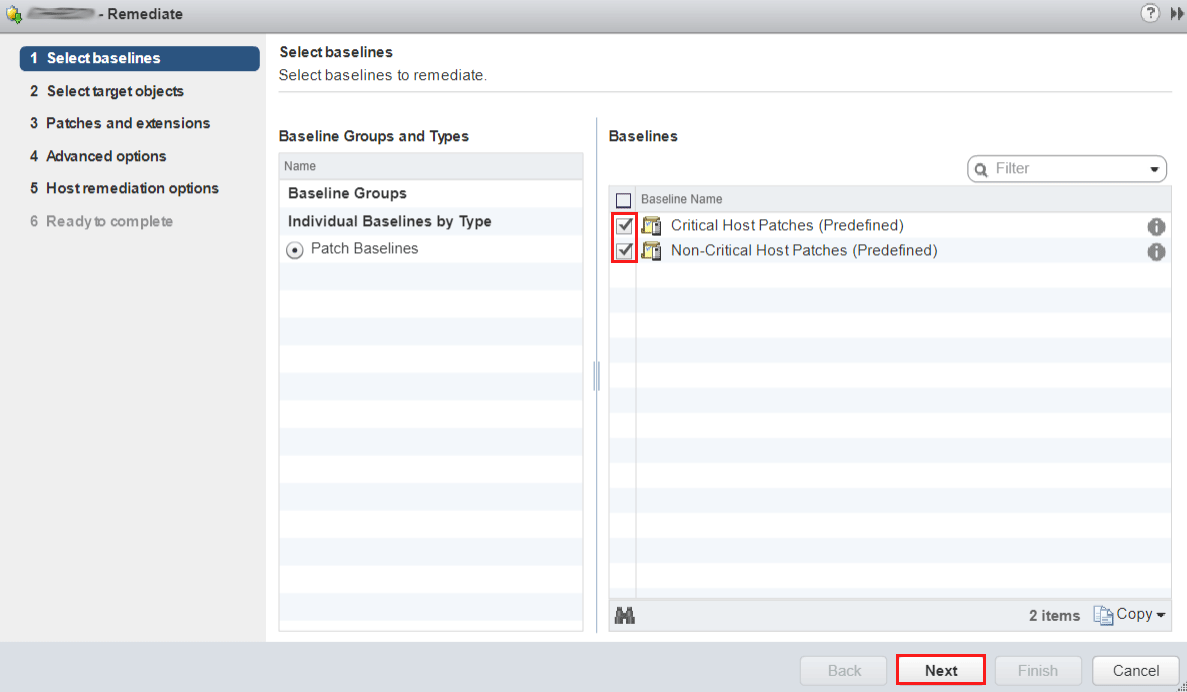
From the Patch Baselines, select Non-Critical and Critical Host Patches. Press OK.
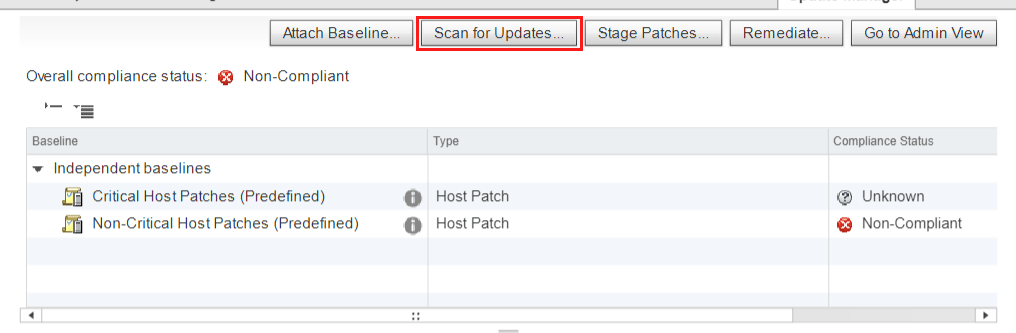
Click Scan for Updates, to verify compliance.
If patching is needed, the compliance status will come back as Non-Compliant.
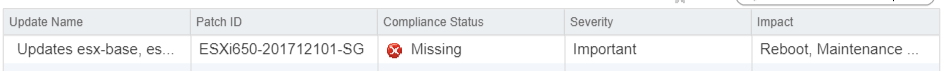
In the non-compliant list, we can see our host is missing the ESXi650-201712101-SG patch.
Next, we will set the remediation options. Click Remediate to begin the process.
Select the patch baselines to remediate.
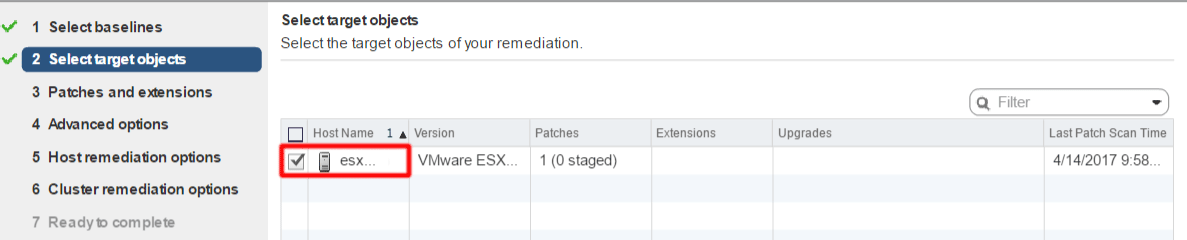
Select the host(s) for remediation.
Select the specific patch to apply.
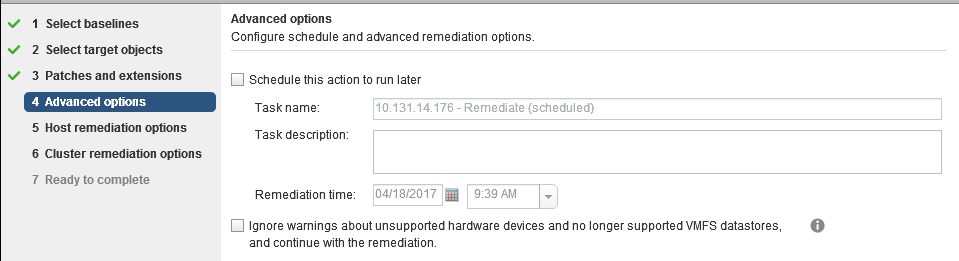
In the Advanced Options section, we can schedule a specific remediation time and/or choose to ignore unsupported items.
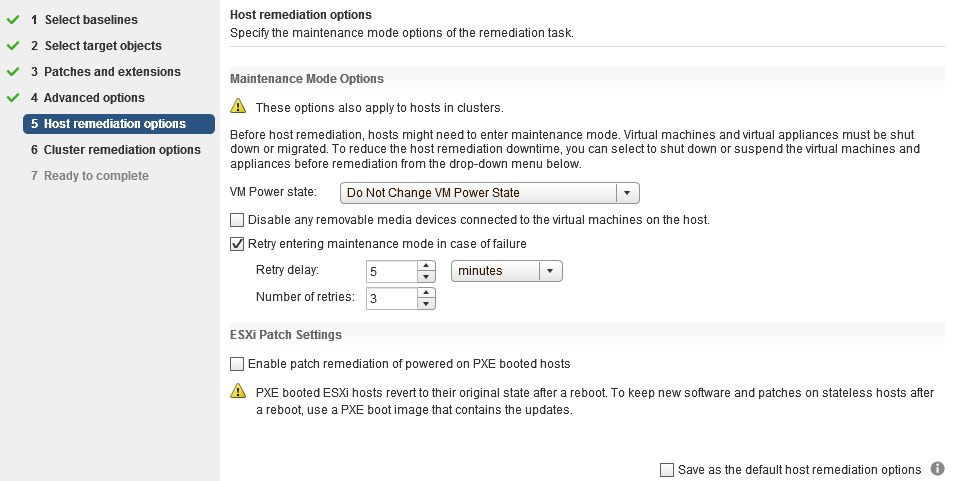
Next, specify Host Remediation Options. Set power state options, disable removable media, and designate maintenance mode retries here.
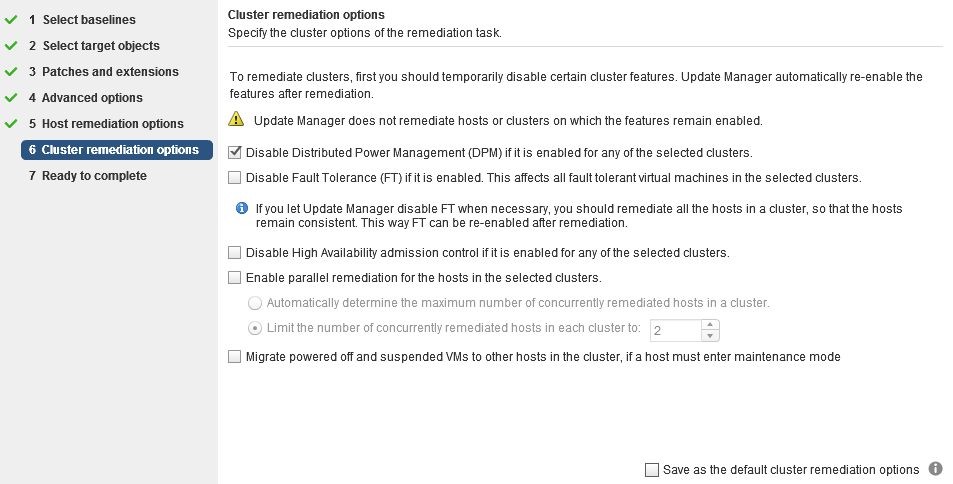
Lastly, specify the Cluster Remediation Options. For hosts in a cluster, the remediation process runs in a sequential manner. If you prefer to run the remediation in parallel, indicate that here.
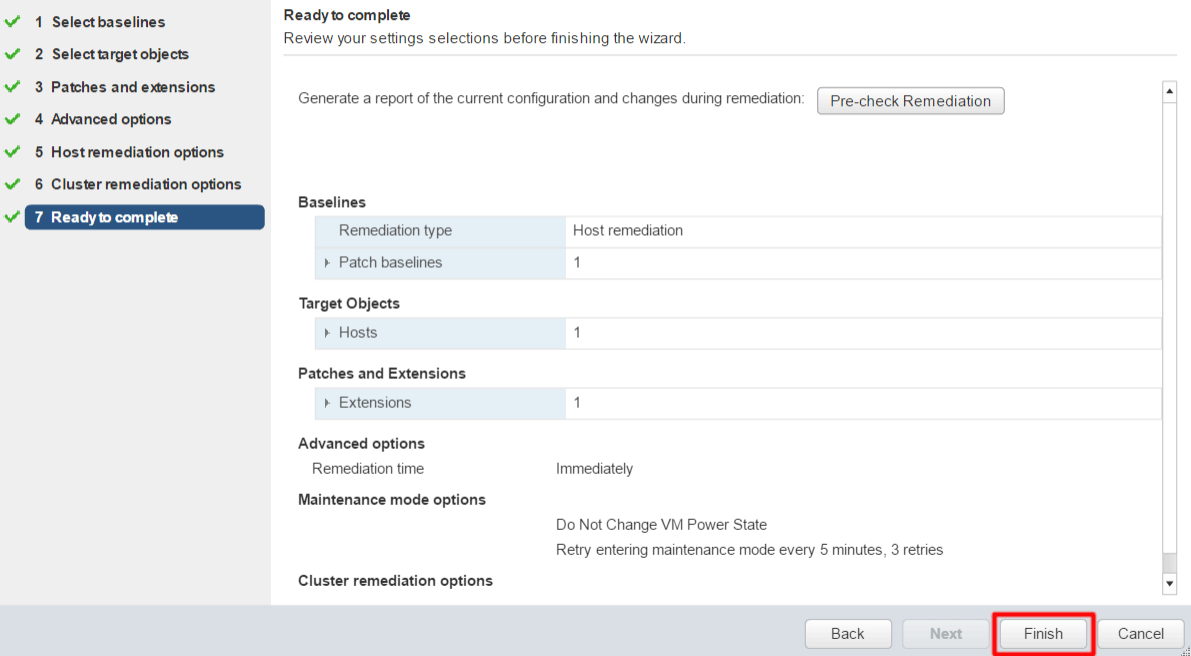
Review selections and click Finish to begin the remediation process.
Progress can be monitored in the Recent Tasks pane. Update Manager performs the following remediation items:
- Enters host in maintenance mode. Migrating virtual machines to other hosts if applicable.
- Applies specified patch.
- Restarts host.
- Re-connects host to vCenter.
- Exits host from maintenance mode.
- Remediates additional host(s) if appropriate.
Once the remediation is complete, the baseline shows compliant.
From early reports, admins will want to patch Guest Operating Systems as well.
VMware Security and Compliance Blog Post – VMSA-2018-0002
VMware Security and Compliance Blog Post – VMSA-2018-0004
Related Posts
29 thoughts on “Spectre Vulnerability – How to Patch VMware ESXi”
Is it needed to patch the OS in all the virtual machines which are running on the patched VM host ?
From what I understand, admins should be patching Guest OSes as well.
If just want to prevent the known VM to VM attack is the host patch enough?
Felix,
From what’s been reported, this patch will remediate known VM to VM attacks. Check out this discussion.
Awesome guide. Does this patch require a restart?
Thanks Wayne! Yes, a reboot is required for the patch.
Thank you for the step by step instructions. Do you know whether we need to patch vCenter appliance as well?
No problem! This KB notes vCenter 6 and 6.5 may be affected. However, they have yet to release a patch.
Update – New vCenter updates (ie. 6.5 U1e) have been released as part of Hypervisor-Assisted Guest Remediation.
the release date of the patch( for esxi 5.5 ) is Release date: September 14, 2017
vmware kown this bug before ?
It sounds like fixes were being worked on before the official disclosure.
Hi
I have created a baseline that include all critical patches for 6.0.
ESXi600-201711401-BG is getting installed but ESXi600-201711101-SG is showing as as obsolete by host.
Does this means that i am still vulnerable?
Found KB that explains this scenario. https://kb.vmware.com/s/article/2041654
When baseline contains security only bulletin and generic bulletin, update manager will install the generic bulletin and mark security only bulletin as obsolete.
This is a great guide. Love the site!
Thanks Jason! I appreciate it!
Have read the hosts need to be patched BEFORE guest updates.
Has anyone done the above and seen any performance hit to ESX or longer CPU scheduling times in their environments?
Thanks
Or impact to VM’s with a high amount of vCPU’s?
What about ESXi 5.1 ? I have a old HP GEN 6 server who is running this version
HP is in the process of rolling new Firmware updates for the various blades. Older, potentially unsupported, equipment may be an issue.
They are indicating February for most of there blades, but i have seen anything other than info about G9/8/7…
VMware still hasn’t released all of the patches yet, so it’s hard to say the true performance impact.
VMware has indicate an “insignificant” change in perform at the hypervisor level.
However, you absolutely need hardware version 9 or higher to help mitigate guest patch performance issues. 11 is prefered…
At least its nit Azure… I understand Microsoft is having a much more difficult time of it.
When I scan I see a patch ESXi650-201712401BG. Could that be it? I do not se the 12101 patch.
Funny… how to get a Vsphere client with ESXi 6.5?
Noway to get that…. have to install the patch manually too bad it is still not in the web client version.
Or am i missing something?
Question about ESXi600-201711101-SG, my update manager says its Obsoleted by the Host What does this mean? Is it installed? I am now to believe my host is not patched.
Thanks for any advice!
it means system already installed newer update that contains one you are trying to install and as result installing ESXi600-201711101-SG is no longer required (has been installed as part of generic update).
What is the difference between the Hypervisor-Assisted Guest Mitigation patch and the one installed here which only patches the host?
I am having a hard time sorting that out. DO you install both…or one or the other?
Folks,
There are three things you need to do, and in a specific order:
– Update you vCenters to the current version
– Update your hosts with the most recent patches (201801401)
– Ensure you’ve applied either OEM firmware updates to your hosts OR apply the VMware microcode Patch (201801402)
Its my understanding that ESXi will update the CPU microcode for processors that are relatively current.
Complete info is here: https://kb.vmware.com/s/article/52085
GB
Folks,
VMware has pulled the patches; only the original patches are now available.
They are recommending that you get firmware updates from your hardware manufacturer, and apply those.
Of course, not all manufacturers are upating all of their platforms.
Still…. how can i update? I use mainly mac’s and have ESXi on a pc system.
How can i update (not now but also in future?
I can not use a vCentre client … however only vSphere server but i need then Windows server and that is not the way.
I can not find a update tab in the webclient when logging onto my ESXi host.
Somebody can help me please?
Comments are closed.