Spectre/Meltdown Vulnerability – How to Patch VMware vCenter 6.5
Variants:
- Spectre-1: Bounds Check Bypass (CVE-2018-5753) – Patch 6.5U1f
- Spectre-2: Branch Target Injection (CVE-2017-5715) – Patch 6.5U2a
- Meltdown: Rogue Data Cache Load Issues (CVE-2017-5754) – Patch 6.5U1f
Patch VMware vCenter Appliance from VAMI
For this example, we utilize URL patching to update vCenter 6.5 to 6.5U1f from the vCenter Server Appliance Management Interface. URL patching will go out to the VMware Repository, check for updates, and patch the VCSA to the latest version.
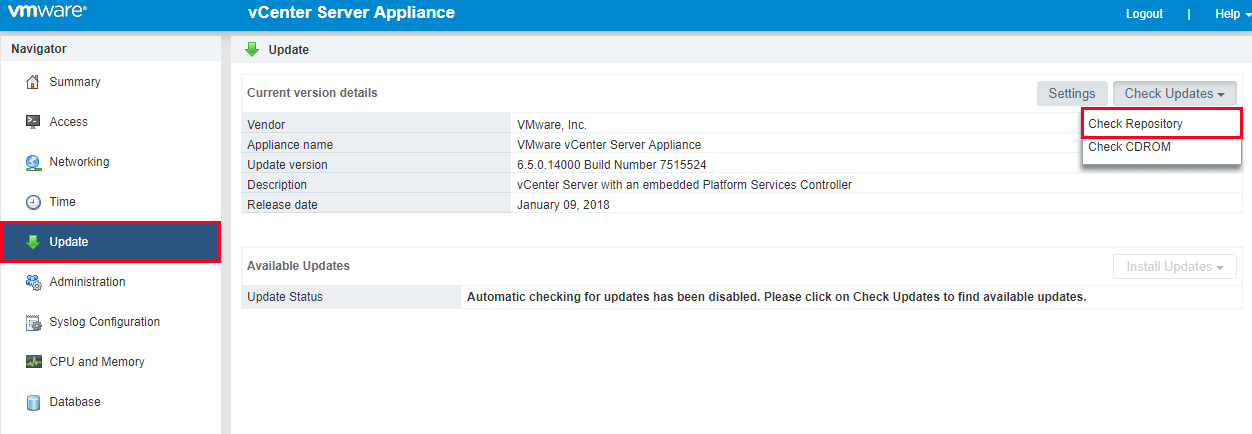
To begin, log in to the vCenter Server Appliance Management Interface at https://vcsaIP:5480. From the Navigator, select Update. Under the Check Updates drop-down, select Check Repository.
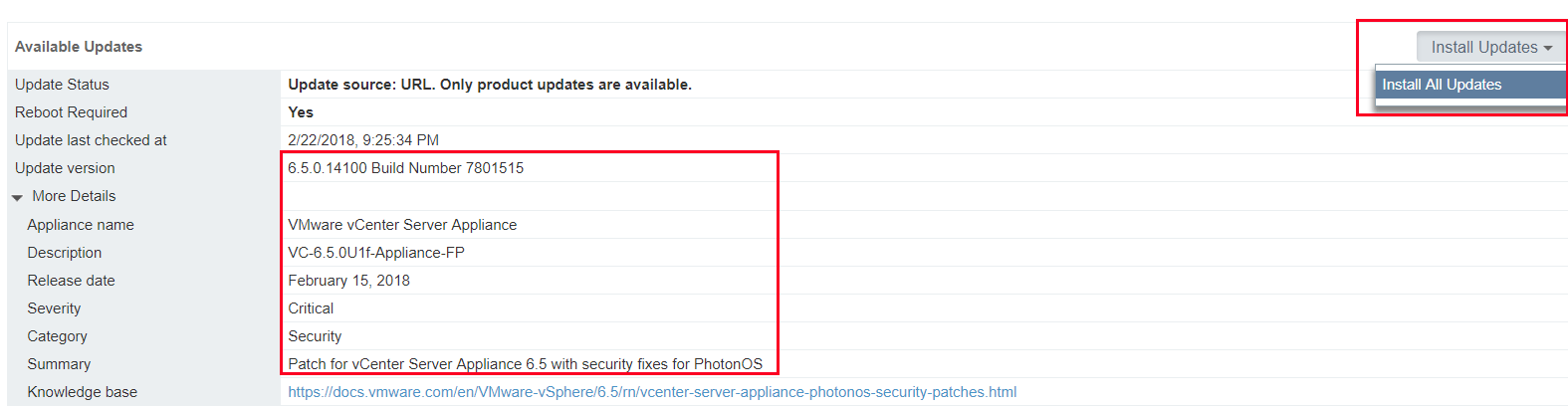
Once the 6.5U1f update has been found, click Install All Updates.
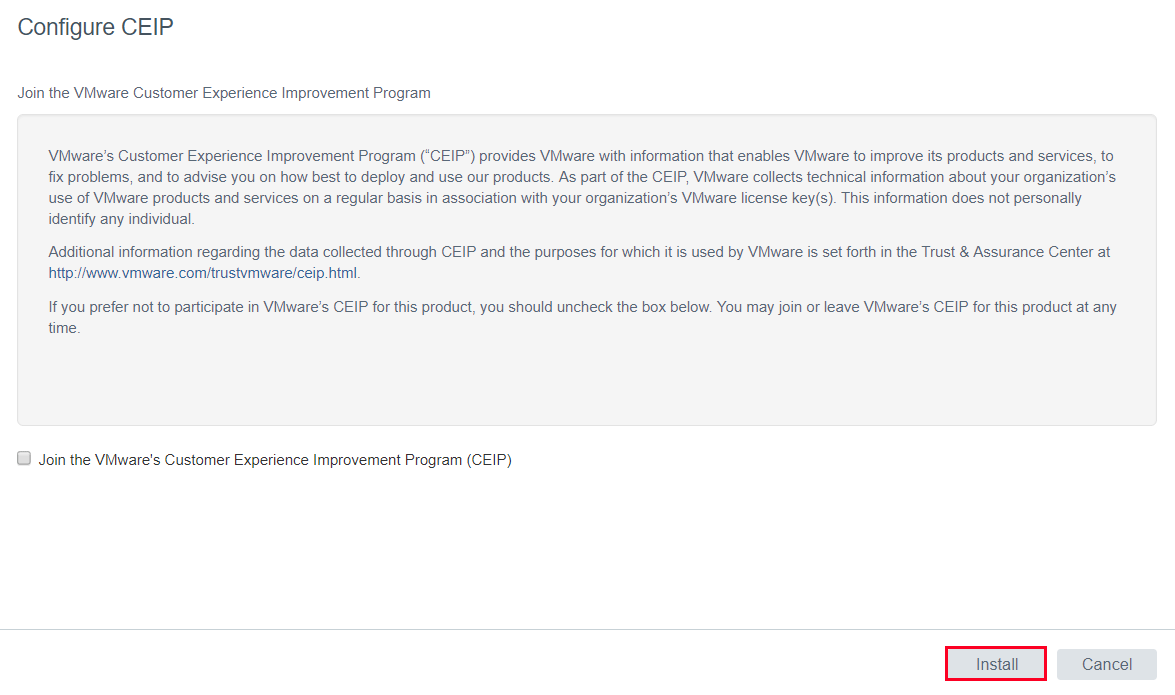
Read and Accept the EULA.
Opt-in or out of VMware’s CEIP and select Install to kick off the update.
Once the update has completed successfully, click OK and reboot the appliance.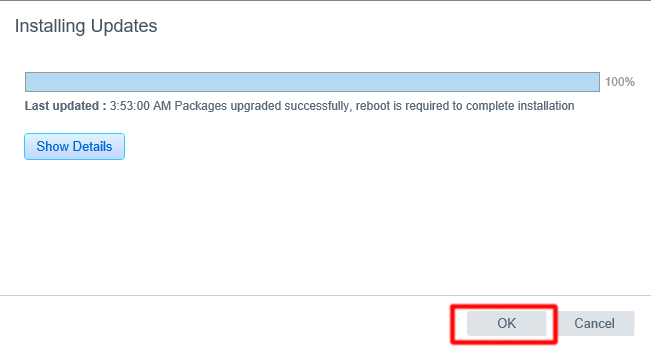
Patch VMware vCenter Appliance from Appliance Shell
If you prefer to update from vCenter’s appliance shell, you can also URL patch the VCSA via the VMware repository.
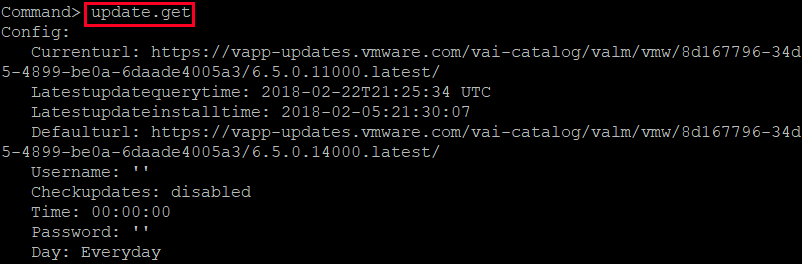
First, we will view the default URL repository and check the last time the appliance polled for patches. To do so, SSH to the vCenter appliance and run the update.get command.
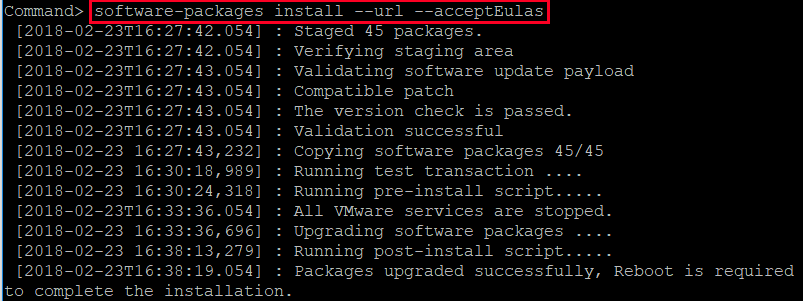
Next, we will run the software-packages install –url –acceptEulas command. This will install patches from the VMware repository and automatically Accept EULAs.
Once the installation is complete, run the shutdown reboot –r “patch reboot” command to reboot the appliance.
Your vCenter appliance should now be patched to 6.5U1f (Build 7801515)!
VMware Security Advisory 2018-0007
Patching vCenter Server 6.5 – VMware Documentation
Related Posts